Open Source Summit is the place to connect directly with the people shaping open source – maintainers, developers, and community leaders, while learning from their experience and insights. It’s an opportunity to discover emerging technologies, explore practical solutions you can apply immediately, and collaborate on ideas and code that drive projects forward. Whether you’re looking to grow your skills, expand your network, or advance your career, the summit offers a unique environment to learn, contribute, and be part of the momentum powering the future of open source.
ELISA project will be represented by our community members at the Safety Critical Track.
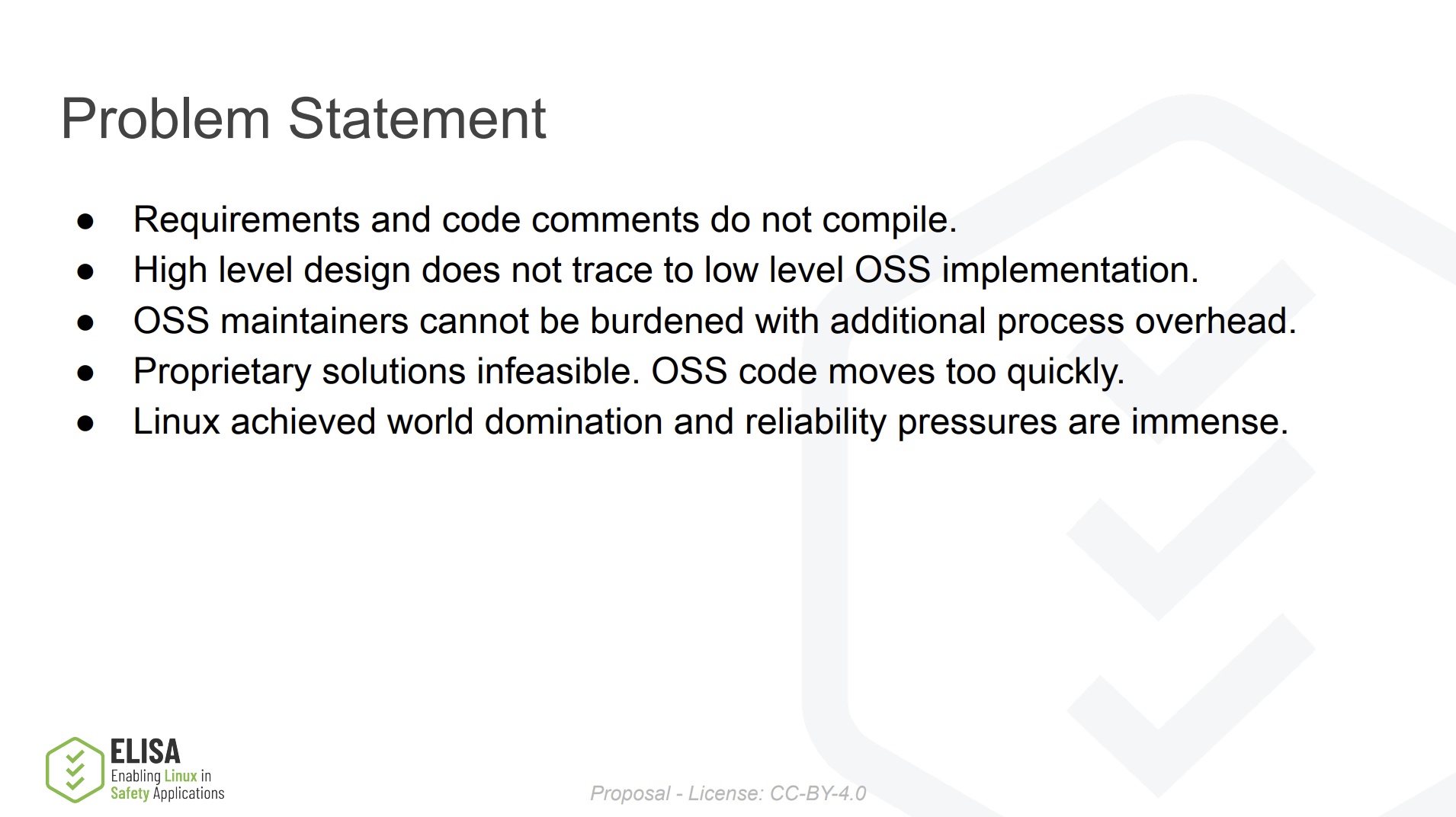
This track explores the intersection of open source and safety standards, covering best practices for regulatory compliance, security updates, and safety engineering. Sessions will delve into requirements traceability, quality assessments, safety analysis methodologies, and technical development for safety-critical systems. Learn more.
Track Highlights:
1. Keynote: Space Grade Linux: Building a Safer, Open Source Future for Space Systems – Ramon Roche, General Manager, Dronecode Foundation
As launch cadence increases and development cycles tighten, the space industry turns to open source to meet the moment. Enter Space Grade Linux (SGL) — an initiative under the ELISA Project aimed at creating a reusable, safety-aware Linux foundation for spaceflight systems.
This talk will introduce the goals and current status of SGL, highlighting three foundational focus areas:
1. Kernel Configuration – Defining a shared starting point for space-focused Linux systems, emphasizing predictability, determinism, and traceability.
2. Booting into Linux: Exploring the safety-critical implications of system bring-up and strategies for improving reliability in space-grade deployments.
3. Userspace Strategy – Discussing early-stage decisions around minimal runtime environments, supervision, and what a safe, maintainable userspace might look like.
Attendees will get a hands-on overview of what’s already available in the GitHub repository, including a Yocto-based reference implementation and working kernel configuration. More importantly, they’ll learn how to get involved — through technical contributions, architecture discussions, or community collaboration.
2. A Human-Centric Quality Assurance Process for Open Source Software Projects – Wendi Urribarri & Carlos Ramirez, Woven by Toyota – Wednesday December 10, 2025 11:10 – 11:50 JST
As autonomous systems become part of our daily environments, ensuring software quality is critical, especially when defects can cause physical harm. In safety-critical domains like automotive, functional safety must be supported by development processes that ensure high quality and reliability, not only for embedded systems but also, in some cases, for software tools.
This talk presents an approach to support quality assurance of open source software projects. What sets this effort apart is the proposed integration of a human-centric quality strategy, rooted in human-error research informed by cognitive psychology and human factors, in the development process of these projects. We introduce a defect prediction engine designed to anticipate common error modes, enabling proactive defect prevention, focused code reviews, and targeted documentation checks. Our approach offers a fresh perspective on improving software quality across domains while aligning with the expectations of safety-critical frameworks.
3. Comparison and Proposal of Vulnerability Management Approaches in Yocto-Based Linux for the CRA – Akihiko Takahashi, Fujitsu Limited – Wednesday December 10, 2025 12:00 – 12:40 JST
Fujitsu has long provided multilateral support for SPDX, especially through activities in Yocto and SPDX. From 2016, we have been joining maintainers of meta-spdxscanner, enabling SPDX functionality for the Yocto Project. In 2024, We joined OpenSSF to enhance the security and trustworthiness of the global software supply chain. This marked a step forward in our continued dedication to this mission.
Due to the EU CRA, manufacturers in the EU will be obligated to report vulnerabilities starting in September 2026. In the context of Yocto, several vulnerability management approaches are being considered, such as cve-check, yocto-vex-check, and third-party tools. However, as of now, there is no clearly established best practice.
In this session, we will apply these vulnerability management approaches to practical use cases relevant to manufacturers covered by the CRA. The comparison includes the use of SBOMs and VEX to evaluate the effectiveness of each method. Through this analysis, we will clarify the strengths and challenges of vulnerability management in Yocto-based Linux and propose which approach is most suitable depending on the context.
4. Driving Safety Forward: Lessons Learned From Deploying OSS in Real-world Automotive – Jaylin Yu, EMQ – Wednesday December 10, 2025 14:00 – 14:40 JST
While OSS in Automotive is seen as the holy grail to solve SDV complexity challenges with faster time to market and higher performance, it still lacks practical real-world examples and showcases that address OSS usage in compliance with the stringent safety and security demands of Automotive.
In this talk, the author shares his real-world story of bringing OSS into mass production vehicles. This includes the impact of a healthy open-source community and how academic research helped solve security gaps, leading to increased system stability. This also embraces the impact of the software supply chain, providing a proven approach, refined through failures, helping to lower dependency risk for MQTT-based remote vehicle diagnostics.
The session is rounded out by highlighting the link between system utilities and safety functions, covering time synchronization, dependency management, and data integrity within a Linux system, which impact the selection of a file system, and what happens when a customer suddenly requires STR.
The audience will leave the session with a holistic impression of what to consider when creating a secure, safe, OSS-based SDV automotive system.
5. Decoding Safe(ty) Linux Architectural Approaches for Critical Systems – Philipp Ahmann, Etas GmbH – Wednesday December 10, 2025 14:50 – 15:30 JST
For years, diverse interpretations about what it means to “enable Linux in safety applications” exist – an observation spanning multiple industries but particularly pronounced in automotive. With its long history of Linux adoption (like AGL) and current software-defined vehicle (SDV) innovation challenges, the automotive sector is undergoing a transition by both manufacturers and suppliers seeking to implement Linux also in safety critical production systems.
This presentation intends to resolve confusion around the terminology “safety Linux” versus “safe Linux”, clarifying where safety responsibility is allocated to Linux itself versus handled at the system level. By examining architectural system concepts currently implemented in products or under development, the author cuts through marketing rhetoric to provide clear distinctions between approaches. It showcases solutions employed by distributors and identifies crucial elements for safety argumentation like watchdog & monitoring.
Attendees will gain practical insights for evaluating safety approaches in Linux-based systems, including key questions to ask when assessing different safety concepts.
6. LF Energy 101: How Open Source Is Powering the Digital Energy Transition – Darshan Chawda & Nao Nishijima, Hitachi -Wednesday December 10, 2025 16:40 – 17:20 JST
The current energy sector must shift from legacy control systems, which are rigid and hardware-bound, to digital, software-defined systems that enable greater sustainability, resilience, and intelligence. To support this transformation, LF Energy, a Linux Foundation initiative, has empowered industrial partners for over seven years to collaborate through community-driven OSS projects, accelerating innovation across the digital energy ecosystem.
This talk offers a beginner-friendly introduction to LF Energy and its key projects, with a demo highlighting their role in virtualizing substations, forecasting energy, and simplifying operations through automation. These projects show how IT and AI technologies enhance grid safety, which is critical because failures in energy systems can disrupt public infrastructure. However, unlike pure IT systems, energy infrastructure relies heavily on physical hardware, making large-scale digital adoption more complex. LF Energy’s open innovation model, focused on IT/OT convergence, helps overcome these barriers by enabling redundancy, virtualization, and collaborative development, which leads to a more reliable and intelligent energy future.
Learn more about the event and register here.






 Elektrobit has been an active contributor to the ELISA Project for several years, and Simone’s appointment reflects the company’s commitment to advancing the use of open source technologies in industries such as automotive, industrial, medical, and beyond.
Elektrobit has been an active contributor to the ELISA Project for several years, and Simone’s appointment reflects the company’s commitment to advancing the use of open source technologies in industries such as automotive, industrial, medical, and beyond.