Last month, the ELISA Project members had the exciting opportunity to attend and speak at both the Open Source Summit Europe and the Linux Plumbers Convention. During these events, we engaged with fellow speakers by asking a series of thought-provoking questions to uncover their insights and experiences within the open source community. Here’s what we found out: from the challenges they faced in their projects to the unique ways they foster collaboration and innovation, the responses painted a vibrant picture of the passion and dedication driving our community forward.
ELISA Project member Alessandro Carminati from Red Hat presented his session, “Addressing Duplicated Symbol Names in kallsyms: Introducing kas_alias for Symbol Differentiation,” at the Linux Plumbers Convention for the first time and also attended the Open Source Summit Europe. He shared, “Both conferences were memorable to me as they were my first experiences at such events.” These events provided valuable opportunities for individuals in the open source community to connect and engage with one another. Alessandro noted, “The networking at Plumbers was extraordinary. Suddenly, all the names I had been seeing on mailing lists became real people. While this might be expected for most, it really amazed me.”

To learn more about Alessandro Carminati and the ELISA Project, we invite you to explore our ongoing initiatives and community engagements. The insights gained from the Open Source Summit Europe and the Linux Plumbers Convention will undoubtedly shape our future collaborations and projects. As we continue to foster connections and share knowledge within the open source community, we remain committed to empowering individuals and driving innovation together. Stay tuned for more updates and opportunities to engage with us as we build a stronger, more inclusive ecosystem for everyone involved.
Incase you missed other ELISA Project sessions from OSS Europe, you can watch all of the session here:
- Application of the Upcoming SPDX Safety Profile – Nicole Pappler, AlektoMetis.com
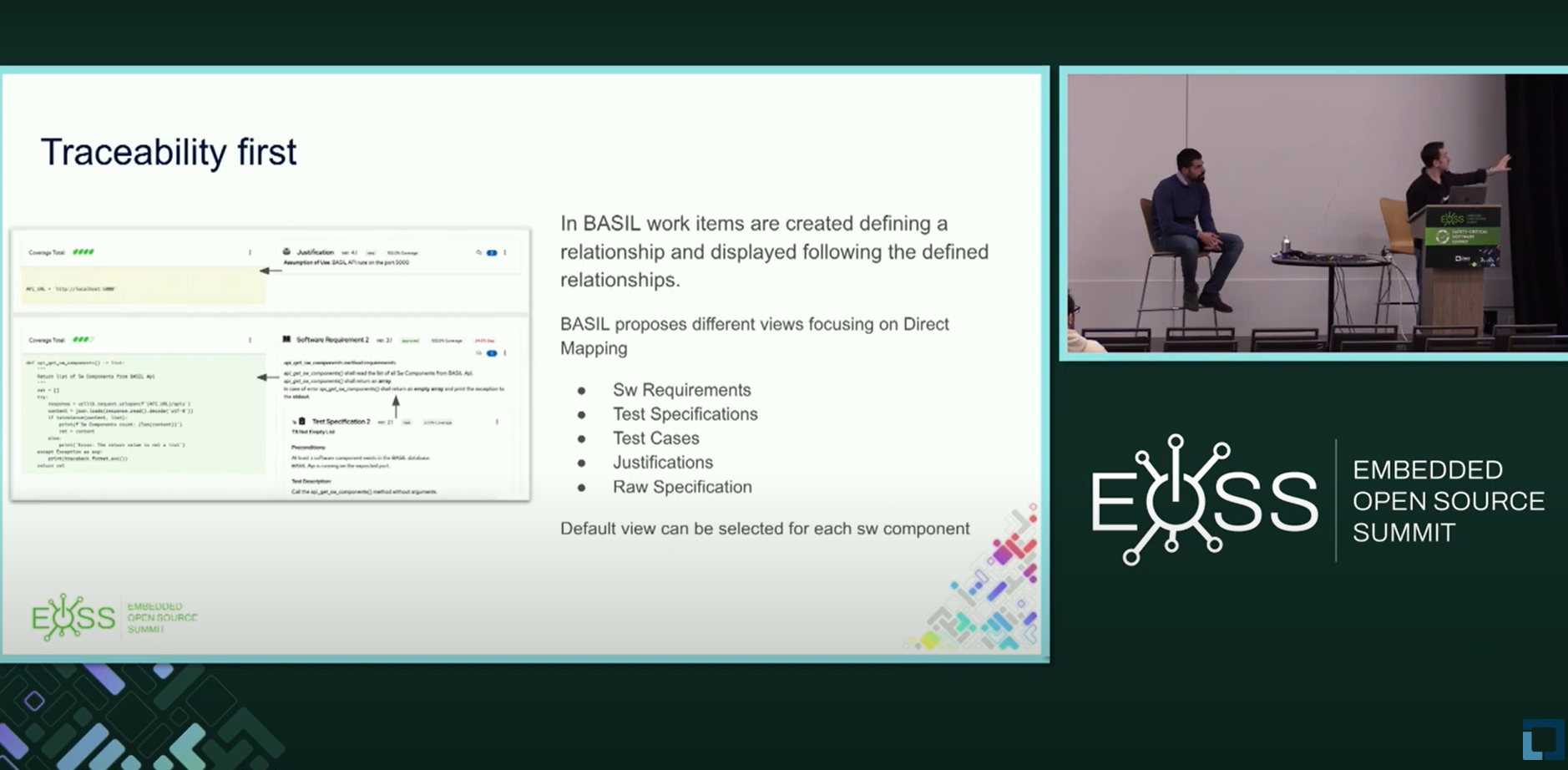
- Traceability and Automation Examples With Basil an Open Source Software for Quality Management – Luigi Pellecchia & Gabriele Paoloni, Red Hat
- Enhancing Kernel Functional Safety Analysis with KS-nav – Alessandro Carminati & Gabriele Paoloni, Red Hat
- Cross Industry Demands and Collaboration Opportunities in Open Source for Safety Critical Systems – Philipp Ahmann, Robert Bosch GmbH & Olivier Charrier, Wind River
- Bridging the Gap: Incorporate OpenSource In Product Managers Toolbox – Philipp Ahmann, Robert Bosch
Stay tuned by subscribing to the ELISA Project newsletter or connect with us on Twitter, LinkedIn or mailing lists to talk with community and TSC members.